OPC-UA Server Endpoint Configuration
EndPoints
Endpoints are always: opc.tcp://$(computername):$(port)
The Server provides following endpoint types:
- None:None:Binary
SignAndEncrypt:Basic256Sha256:BinarySign:Basic256Sha256:BinarySignAndEncrypt:Aes128Sha256RsaOaep:BinarySign:Aes128Sha256RsaOaep:BinarySignAndEncrypt:Aes256Sha256RsaPss:BinarySign:Aes256Sha256RsaPss:BinarySign:Basic256:Binary(Deprecated)
Certificates
Communication and authentication can be secured by x509 certificates. All certificates are stored locally in the certificate store, either in a directory structure (default) or in the Windows Certificate Store (only Windows systems).
The OPC-UA server has to manage several different certificates:
-
Server Certificate (also called application certificate): It's the owner certificate of the OPC-UA Server
- Directory: put it into the
ownfolder - Windows: put it into the
LocalMachine\Myfolder
- Directory: put it into the
-
Client Certificate (application certificate of the UA clients)
- Directory: put it into the
Trustedfolder - Windows: put it into the
LocalMachine\Trustfolder
- Directory: put it into the
-
User Certificate used for Authentication
- Directory: put it into the
Trustedfolder - Windows: put it into the
LocalMachine\Trustfolder
- Directory: put it into the
StoreType Directory
The default location is Config\HumanOS.PeSeL.OPCUAServer\CertificateStores.
This can be overwritten with the setting CertificatePath.
Absolute or relative paths can be used, variables from the HumanOS appsettings.json can also be resolved.
It contains following sub folders:
Own: own and self-signed certificatesIssuer: issuer certificatesTrusted: trusted certificatesRejected: rejected certificates
StoreType Windows
For windows certificate store, each subfolder can be configured individually:
CertificatePathis the owner folderCertificateTrustedPathis the folder with trusted certificates (typicallyLocalMachine\Trust)CertificateIssuerPathis the root certificate authority folder (typicallyLocalMachine\Root)CertificateRejectedPathis the rejected certificate folder (typicallyLocalMachine\Disallowed)
The folder name does not match with the display name of the "Windows Certificate Store Application".
Available store locations can be queried with powershell:
- Computer
Get-ChildItem Cert:\LocalMachine - User
Get-ChildItem Cert:\CurrentUser
Listing the contents of a specific certificate by thumbprint, whereas the subject is what we want for the CertificateSubject in configuration:
Get-ChildItem Cert:\LocalMachine\Root\<mythumbprint> | select *
Remember that some locations in 'LocalMachine' require UAC privileges and therefore can only be accessed if the software runs in an elevated context or the permissions are set correctly on the private key. If e.g. the error 'One or more errors occurred. (Keyset does not exist)' is thrown, this means that either the keyset really doesn't exist, or the permission is not sufficient. To set the permission open certlm, navigate to the certificate, right click on it -> all tasks -> manage private keys and add the user or user group with read permission. Remember that locations like 'LocalMachine\Root' cannot be permission edited.
Generating a Server Certificate
The server certificate is used for secure communication channels and must match following settings:
- Name: Used to create the subject name
CN=$(Name)/O=UnifiedAutomation/DC=$(hostname) - ServerURI
Use the certificate generator from unified automation: Opc.Ua.CertificateGenerator.exe (check Certificate generator for more information).
Make sure you are generating the certificate with the key size
2048. The default of 1024 is insufficient to run the secure endpoints of the OPC-UA Server.
Example:
Creates a certificate for OPC-UA Server on host myhost and puts the file to the certificate store of the HumanOS® OPC-UA Server
.\Opc.Ua.CertificateGenerator.exe -cmd issue
-au "urn:myhost:HumanOS:OpcUaServer"
-sn "CN=HumanOS OPC-UA Server/O=UnifiedAutomation/DC=myhost"
-sp "C:\Temp\CertificatePath\OPCUACertificateStores\own"
-dn myhost
-an "HumanOS OPC-UA Server"
-st ([datetime]::Now).toFileTime()
-ks 2048
Remember to install the certificate in the windows store if using store type 'Windows'.
Arguments:
-au: application uri (must match the setting of thesettings.json)-sn: subject name (CN must match the name setting in thesettings.json)-sp: location of the own-certificate store of HumanOS installation-dn: domain name of the server-an: application name (must match the name setting in thesettings.json)-st: start time of the certificate-ks: key size (min. 2048)
When starting HumanOS®, following log-output should show the different endpoints with the secure connections:
2021-02-20 21:41:17.835 [INF] OpcUaServer: Startup OpcUaNodeManager
2021-02-20 21:41:17.965 [INF] OpcUaServer: Endpoint [opc.tcp://CLI07-GWA-CTECH:4840/ [SignAndEncrypt:Basic256Sha256:Binary]]: Status = Good
2021-02-20 21:41:17.970 [INF] OpcUaServer: Endpoint [opc.tcp://CLI07-GWA-CTECH:4840/ [Sign:Basic256Sha256:Binary]]: Status = Good
2021-02-20 21:41:17.976 [INF] OpcUaServer: Endpoint [opc.tcp://CLI07-GWA-CTECH:4840/ [SignAndEncrypt:Aes128Sha256RsaOaep:Binary]]: Status = Good
2021-02-20 21:41:17.978 [INF] OpcUaServer: Endpoint [opc.tcp://CLI07-GWA-CTECH:4840/ [Sign:Aes128Sha256RsaOaep:Binary]]: Status = Good
2021-02-20 21:41:17.981 [INF] OpcUaServer: Endpoint [opc.tcp://CLI07-GWA-CTECH:4840/ [SignAndEncrypt:Aes256Sha256RsaPss:Binary]]: Status = Good
2021-02-20 21:41:17.984 [INF] OpcUaServer: Endpoint [opc.tcp://CLI07-GWA-CTECH:4840/ [Sign:Aes256Sha256RsaPss:Binary]]: Status = Good
2021-02-20 21:41:17.991 [INF] OpcUaServer: Endpoint [opc.tcp://CLI07-GWA-CTECH:4840/ [None:None:Binary]]: Status = Good
2021-02-20 21:41:17.995 [INF] OpcUaServer: Server is running
BadCertificateUntrusted
Self-signed certificates typically give the following error on the OPC-UA client side, like UAExpert:
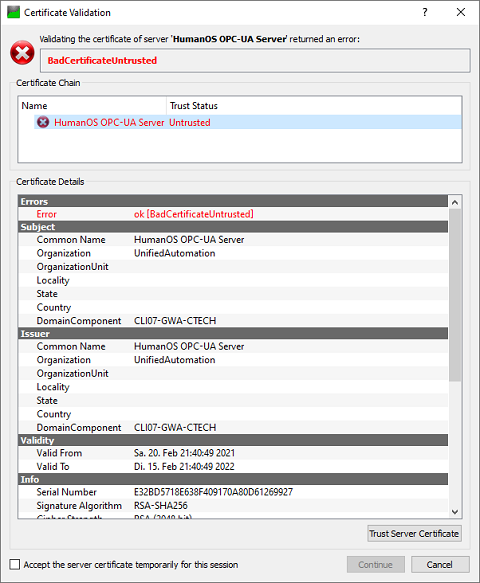
You can manually accept the certificate. Be aware that the some clients do not check the windows store, only directory or GDS/LDS stores.
Authentication
The server supports following authentication procedures:
- Anonymous: anyone can communicate with the OPC-UA server.
- Username and password
- Certificates
Username and Password
The username and password procedure uses the local system Logon-procedure of Windows®. Its possible to authenticate local or AD users.
Logon on the Windows with this user first, to create the user profile in the local system.
Certificates
The OPC-UA Server supports the authentication with certificates.
Copy the *.der file to the CertificateStores\trusted\certs folder.
For store type Windows, install the client certificate to the CertificateTrustedPath, like LocalMachine\Trust (Enterprise Trust).