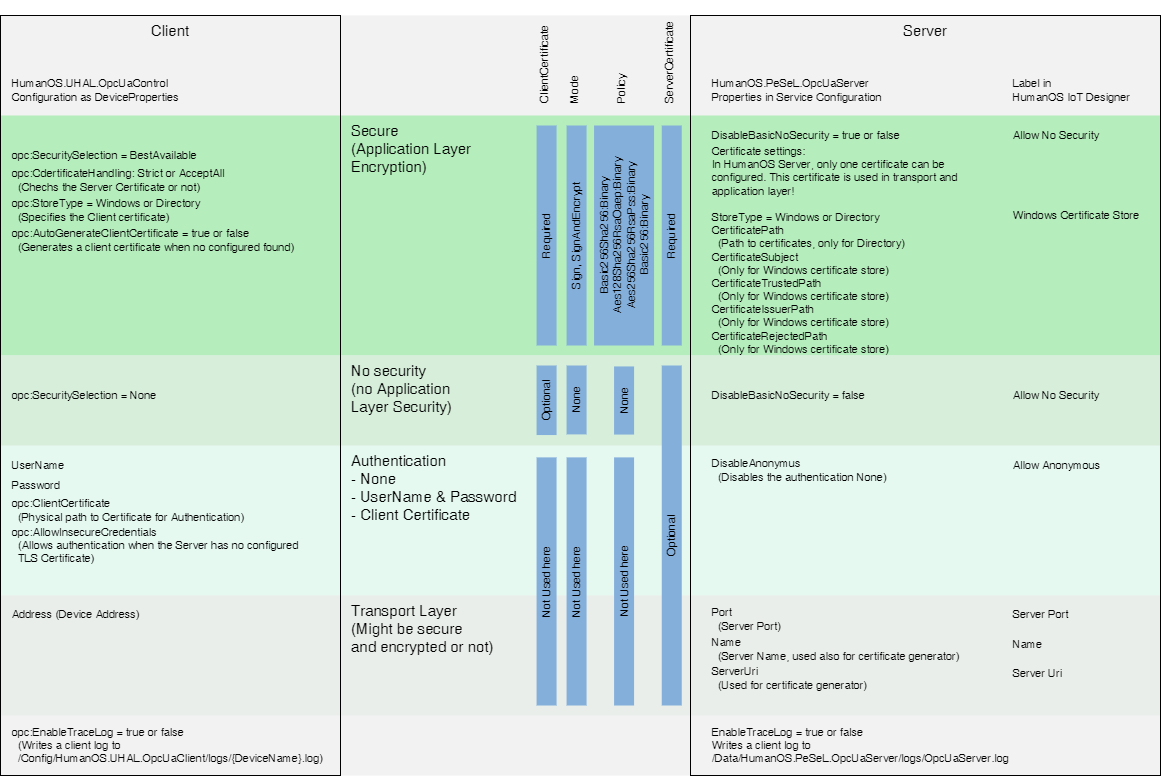
OPC-UA Connection Overview
The following image is intended to provide a quick overview of the OPC-UA protocol. In addition to the plugin manuals, this page is intended to help configure the connections in HumanOS.
The settings for the OPC-UA client are described on the left.
To the right of the OPC-UA server.
The security features of OPC-UA are arranged in the middle.
The green background describes the application layer and the gray background describes the TLS layer.
Encryption
OPC UA allows to configure a combination of different security mechanisms to encrypt communications and ensure security.
-
Transport Layer Security (TLS): OPC UA can use TLS as a transport protocol to encrypt data during transmission. TLS provides a secure communication layer over TCP/IP and ensures confidentiality, integrity and authenticity of data transmission. Authentication with OPC-UA is handled in the transport layer.
-
Application layer encryption: (Endpoint Encryption) In addition to transport encryption, OPC UA also offers the ability to encrypt data at the application layer. This allows for an additional layer of security.
The same certificate is typically used for TLS encryption and endpoint encryption in the OPC UA protocol. This certificate is provided by the OPC UA server and typically contains information such as the server name, the server's public key, the issuer of the certificate and other relevant details.
Authentication options
The Authentication options are provided in the transport layer.
-
No Authentication (None): This allows a client to authenticate to the server without providing credentials. In other words, this method allows a client to access an OPC UA server without presenting a username, password or certificate.
-
Username and Password: This is a simple form of authentication that requires users to prove their identity by entering a username and password. OPC UA supports the transmission of username and password over encrypted channels to ensure security.
-
Certificate-based authentication: OPC UA can use certificates to authenticate clients and servers. A client can use a certificate to verify its identity to a server, and vice versa.
Message Security Mode
The Message security mode defines the encryption at the application layer
-
None: No security features are applied in this mode. Data transmission is unencrypted, which is only recommended for test purposes, in secure networks, when no confidential data is exchanged or when you already have encryption at the transport layer (enabled TLS).
-
Sign: In this mode, messages are digitally signed to ensure their integrity. The signature uses asymmetric encryption techniques and allows the recipient to verify whether the message has been tampered with during transmission. This technique requires certificates.
-
Sign and Encrypt: This mode includes both signing and encrypting messages. In addition to ensuring integrity, the confidentiality of the data is also ensured through encryption. Encryption uses symmetric encryption techniques to improve efficiency and takes place at the application layer which is described in section Encryption.
Advantages
By using multiple levels of encryption, various security goals can be achieved:
-
Protection against attacks: By using different encryption methods at different levels, it becomes more difficult for potential attackers to exploit security holes. Even if an attacker compromises one layer of encryption, they still have to overcome additional obstacles to access the data.
-
Increase security: By combining different encryption techniques, vulnerabilities can be mitigated in a single method. For example, application-level encryption can be used in addition to transport encryption to achieve a higher level of security.
-
Flexibility and compatibility: Different systems and applications can support different encryption protocols. By implementing multiple layers of encryption, OPC-UA can ensure compatibility with various security requirements and standards.